Forms are the backbone of user interaction on the web. Unfortunately, this also means they're a prime target for spam bots that flood your backend with fake submissions. A honeypot field is a simple, cost-effective security technique to prevent this - while being completely transparent to real users (unlike CAPTCHA).
Why do we need to prevent bot submissions?
At first glance, isolated bot submissions may seem harmless. But when they accumulate, the effects can be considerable:
- Bots can flood your analytics and storage with useless data, leading to higher costs.
- Massive bot traffic can overload servers, causing outages and impacting service for real users.
- Bot submissions can serve as an attack vector to spread malicious links and put your users at risk.
The honeypot field strategy
The principle behind a honeypot field strategy is simple: you add a hidden input field to your form that real users do not fill in - but bots do, as they are programmed to fill in every field. If the hidden field is filled in, this is a clear sign of a bot submission and can be discarded without hesitation.
The term honeypot is particularly apt here - just as honey attracts insects in the real world and traps them in its sticky trap, bots can't resist filling in any field, including the invisible honeypot field. Just as honey catches insects, the honeypot field catches bots and makes it easy to identify and discard their fake submissions.
A major advantage of this method is that it does not affect the user experience. Unlike CAPTCHAs or other visible bot protection mechanisms, there are no annoying pop-ups or modals that require multiple clicks (often causing users to abandon the process in frustration). The downside is that advanced bots specifically designed to bypass such traps could still get through. Nevertheless, the honeypot strategy remains a simple and effective way to block a large proportion of bot traffic.
Let's set the trap and stop the annoying bots!
How does this manifest itself with Odoo?
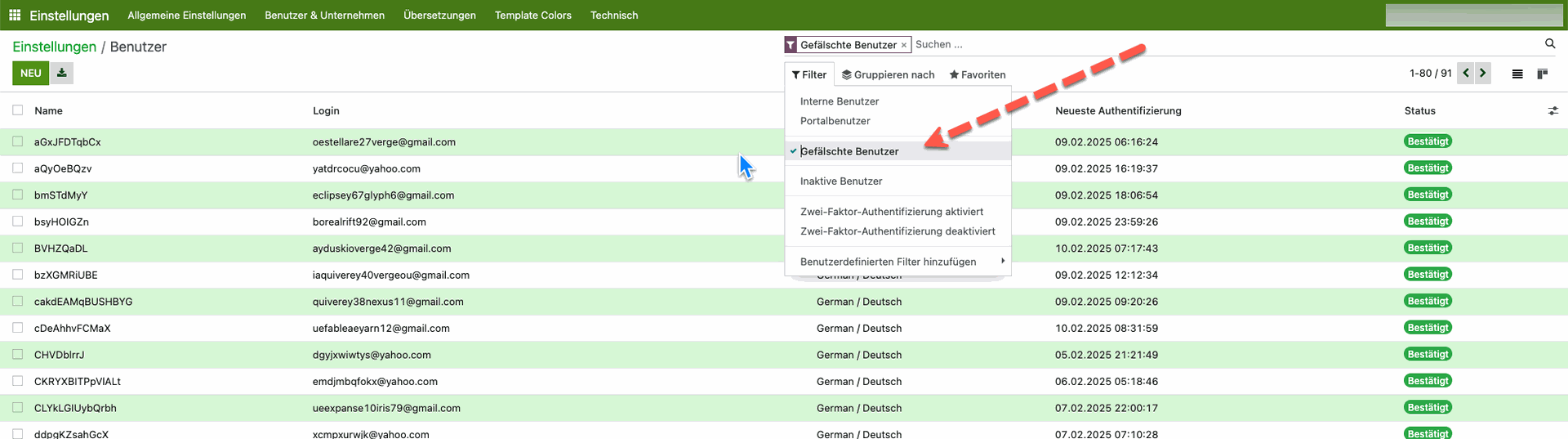
We have noticed that so-called fake users have been appearing in various customer systems over the past few weeks. These could be easily recognized by their names, as they consisted of randomly connected characters. It was also noticeable that these fake users were even logging into the system. Email addresses with Gmail and Yahoo domains were particularly common. The background to this is probably that more attempts are being made to penetrate the system.
This means that it was not the contact form that was misused by these bots, but the registration form, especially in Odoo systems that also had a web store. Fake users were practically created and it was tested whether the system had vulnerabilities and whether there was a gateway into the system.
Even if the system had no vulnerabilities, these bots placed a heavy load on the system. On the one hand, new users were constantly being created, which of course also meant that contact details were being created. Secondly, an e-mail was sent each time, and the bots probably also tried to log in. In short, the system was brought to its knees and possibly had the disadvantage that it could be infiltrated if it was not patched regularly.
Our modules for an Odoo solution?
We have developed two modules. Firstly, we have protected the registration form using the honeypot field strategy. Secondly, we have developed a module with which fake users can be identified and subsequently deleted. Previously, you first had to delete the entry in the contact details before you could remove the linked user. With our module, both are possible at the same time.
Future
Once we have developed effective protection with these two modules, we will also transfer the modules that we have ported for versions 13 and 16 to other Odoo versions and then make them available in the Odoo store if necessary. Before we do this, however, we will test for a few weeks whether effective protection actually exists.
Another option is, of course, that if a so-called fake user does get through the honeypot, we not only identify them via the second module with the fake users, but also block them. In this way, the user can first check this user before he even gains access to the Odoo system.
If you have noticed similar problems in your odoo system, please feel free to contact us. Perhaps our collection of modules will help you.